
Cybercrime is a growing industry. Every 39 seconds, there’s a new cyberattack somewhere on the web. These aren’t just targeted attacks at major industries and name brands. If you’re connected to the internet, you’re a potential target.
So, what can you do to protect your company data from cybercriminals?
In the last ten years, both cybercrime and cybersecurity have changed drastically. New tools and procedures—particularly cybersecurity frameworks like NIST and CIS—developed in direct response to threats from the cybercrime industry.
Utilizing a cybersecurity framework increases the efficiency of your cybersecurity tools and process to better protect your network, systems, data, and reputation.
WEBIT Services created SecureBIT to help businesses simplify security. We are passionate about using education, not fear, to help companies make informed IT Security decisions and investments based on facts and their risk tolerance.
By reading this article, you will learn how frameworks help users to match tools and processes to their needs and how it helps increase cybersecurity.
Tools need a framework
Ten years ago, all you needed to protect your data was antivirus, firewall, and backups. Now, you can use dozens of tools to protect your systems.
However, Tools will not reach their full potential if you do not follow a cybersecurity framework like NIST or CIS.
Frameworks were created in direct response to the cybercrime industry in the early 2000s, and they lay out reliable, trusted procedures and recommended tools to identify and address risks.
Frameworks are also frequently tested and revised to ensure they are relevant, effective, and efficient in addressing old and new cyber threats.
Frameworks teach you how to use the tools
If you’re not following a framework, your cybersecurity tool may be used incorrectly and not bring you the protection you need.
Let’s say you want to build a gazebo in your backyard. To do this well, you’ll need a blueprint, the proper tools, and instructions on or knowledge of how to use the tools.
Now, you can buy an excellent drill for this project. However, this drill isn’t effective if you use it on the wrong materials. It’s also no help if you use the drill as a hammer instead of a drill.
And how is it helpful if you leave the new drill in its packing and never take it out?
Your gazebo will not be built well unless you follow instructions and use tools as intended.
A framework is a blueprint for your cybersecurity system. It tells you when, where, and how to use cybersecurity tools to address risks.
Framework cybersecurity stages
All frameworks define the stages of effective cybersecurity and the tools best suited for each task. While the terminology may vary across each framework, the core instructions can be summarized as follows:
- Identify or Inventory hardware, software, and practices in use.
- Protect the system through various tools and practices.
- Detect or track threats.
- Respond to or correct detected threats.
- Recover system functionality and data loss, if possible.
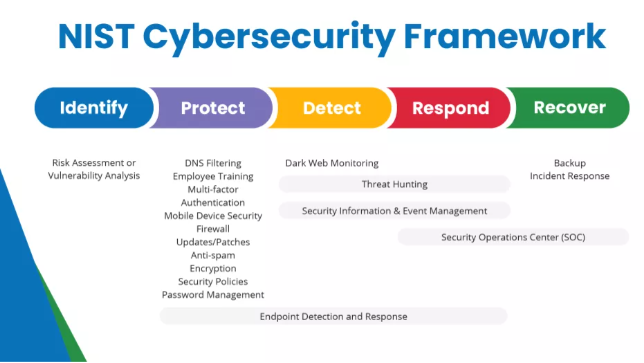
1. Identify technology
If you don’t know what you’re protecting, how can you protect it?
Therefore, it’s vital to identify all IT assets within your organization. All hardware, software, and systems must be identified to be protected.
If one laptop or tablet isn’t recognized and added to your cybersecurity system, it creates a vulnerability. It can open your organization to attack.
Following a framework, your IT provider or internal IT team has designated tools to run assessments to identify your assets and any associated risks.
2. Protect your system
Ten years ago, all you needed to protect your data was antivirus, firewall, and backups. Now, “antivirus” is an antiquated term. Instead, cybersecurity systems use “endpoint protection”—a series of tools to counter cyberattacks.
Frameworks recommend the following endpoint protection tools to help guard identified hardware and systems:
- Firewall
- DNS filtering
- Password management
- Multi-factor authentication
- Anti-spam programs
- Mobile device security
- Software and operating system patches and updates
- Data encryption
- Security policies
- Employee training
A wide range of products and services meet these security requirements. Each tool has a unique function in protecting your data.
Firewalls
Firewalls act as the “front door” to your network. It examines packets of data coming into your network and blocks packets from threatening sources.
DNS filtering
DNS filtering allows your organization to block access to specific sites. These sites may be blocked as security risks to prevent potential malware downloads.
Password management
Good password management practices help keep login information safe. It applies principles like:
- Create a robust password of 12 or more characters.
- Use a combination of uppercase and lowercase letters, numbers, and symbols.
- Change your password regularly.
- Do not share your password.
More complicated passwords make it more difficult for cybercriminals or their AI software to guess login information correctly and access your system.
Multi-factor authentication
Multi-factor authentication (or two-factor authentication) makes it more difficult for cybercriminals to hack into your system or accounts. Even if they have an employee’s login credentials, they cannot enter your network if they don’t have the authentication code.
Anti-spam programs
Anti-spam programs help reduce spam emails and phishing attacks.
Spam and phishing emails are social engineering tools. Social engineering tries to gain login credentials from users so cybercriminals can infiltrate networks. Unfortunately, it is still the highest source of security breaches.
In 2021, 98% of cyberattacks relied on social engineering.
Reducing the number of dangerous emails in your inbox also reduces your infiltration risk.
Mobile device security
Mobile devices need security settings and protections like laptops, particularly if used professionally to enter the business network.
This includes security policies like setting a login password for your device and setting up a remote memory wipe if the device is lost or stolen, protecting confidential company data.
Software and operating system patches and updates
Software companies regularly test for vulnerabilities in their products, and they release patches to address these weaknesses.
If you’re not patching your software, it can be breached.
Data encryption
Encryption tools scramble text into a secret code to protect it from cybercriminals. Essentially, stored data or data sent to other users is encrypted. So even if the data is intercepted, only people with the encryption key can read it.
Security policies and employee training
Regular training and effective policies help keep cybersecurity front of mind and create a culture of security. In addition, both security policies and employee training help minimize potential human error.
Security policies establish security standards and practices for the company. Policies may be determined by the individual organization or regulated industry compliance standards.
Employee training addresses risk trends among users. For instance, if you notice a high click rate for phishing emails, your company may train employees to recognize phishing attempts and secure email use.
3. Detect threats
Cybersecurity frameworks include “threat detection” as a vital step in the security process. Detecting threats allows you to address and remove them before they cause significant damage.
Cybersecurity is not a “set it and forget it” practice. Instead, you establish defenses, regularly look to improve them, and detect any threats that may have come through.
There are a wealth of tools built for threat detection.
In addition, your IT provider or internal IT department will run quarterly risk assessments to detect new risks and potential threats.
4. and 5. Respond and recover
When you face a cyber threat, frameworks recommend having tools to remove the danger and an incident response plan to reduce downtime and bring your system back online.
An incident response plan helps minimize financial losses resulting from system failure.
Frameworks also recommend having data backups and continuity plans in place to help prevent data loss.
Next steps for using a framework in cybersecurity practices
Cybersecurity frameworks like NIST and CIS grew in response to the increasing number and damage of cyberattacks. They created guidelines for cybersecurity frameworks summarized as the following steps:
- Identify
- Protect
- Detect
- Respond
- Recover
Each step has a collection of recommended tools and processes to meet its goal.
Cybersecurity has grown more complex and requires more specialized skills and knowledge. As a result, many businesses hire Managed Security Services (MSS) or IT providers that are a hybrid between managed services and managed security.
Speak to your IT provider or internal IT team to learn more about the framework they used to create their procedures and determine their tools.
If your IT provider or team does not follow any framework, that is cause for concern. They could be missing a critical step in protecting your company’s data. This could also indicate that it’s time to find a different provider.
WEBIT Services has been identifying and managing risk for small to medium sized businesses for almost 30 years.
If you’re looking for security answers, book a call with our team to see how SecureBIT can help simplify security.
If you are not ready to make a commitment but want to learn more about cybersecurity, we recommend the following articles:
- CIS and NIST Frameworks | Why they matter in a risk assessment
- 7 Tips for building a culture of cybersecurity
- Is my business secure? | 6 cybersecurity practices to know
- Cybersecurity Risk Levels: Where do you draw the line?
- Managed IT vs. Managed Security vs. Compliance: What are the differences, and where do they overlap?
